Screen Locks Are a Form of Endpoint Device Security Control
Removable Media may transfer malware to computers and can also be used to extract. Answer to Solved Screen locks are a form of endpoint device security.

Remotely Lock Your Device From The Intune Company Portal App Microsoft Docs
Screen after 2 minutes of inactivity.
. When you send a security policy such as a lock or a wipe Endpoint Management processes the policy on the device the next time the device connects. A key lock or an equivalent control eg. A settings conflict occurs when a device receives two different configurations for a setting from multiple sources.
Endpoint device control is critical to protecting organizations data assets from the risks associated with the use of removable devices. Trojans and viruses can be brought in on them defeating nearly all of the network-based anti-virus measures implemented. Device restrictions and security requirements.
Hi all I cant seem to get the screen lock or desktop image to work through intune I use a URL which is the location of the image which I save in sharepoint. Screen locks are a form of endpoint device security control. In todays age of small portable storage devices the risk introduced into the network by these devices is large.
Endpoint and Device Security. Asset tag information for the device. A basic MDM Mobile Device Management software focuses on management of devices.
Prey is a cross-platform Device Tracking Security tool to stay in control of remote assets. The best form of action is to be proactive and lock down any opportunity that one will download onto your computer. Marked as answer by CloudTester Tuesday July 24 2018 1143 PM.
This means you must avoid going to questionable sites and using an advanced scanner like Comodo Advanced Endpoint Protection to shut down lock screen ransomware before it. The Microsoft 365 security portal shows removable storage blocked by the Device Control Device Installation. Enter the length of time a device must be idle before the screen is locked.
Did you try the Device Configuration profile for Windows 10 and later. From the Overview page of a device you can then select Endpoint security configuration to view the endpoint security policies that apply to that device. The business impact analysis BIA identifies the resources for which a business continuity plan BCP is necessary.
Policy details are available for devices managed by MDM and Intune. HIPAA 164312a The device automatically locks. Device Control is the branch of endpoint security that refers to the control of devices access to computers.
Any ideas why it doesnt display. To access the Microsoft 365 security you must have the following subscription. Screen locks are a form of endpoint device security control.
I use this link on open in a browser to make sure it works and opens correctly so its not a broken link. Endpoint Management attempts to reconnect the users device to the Endpoint Management server after a network connection loss. Remote wiping is a device security control that allows an organization to remotely erase data or email in the event of loss or theft of the device.
Controls devices apps and security in one interface. The document can also address expected security configurations required by IT to permit the device to be used for work-related activities and to interact with. Endpoint protection Local device security options Interactive Logon Minutes of lock screen inactivity until screen saver activates.
Ensure that everyone is safe. For example enter 5 to lock devices after 5 minutes of being idle. Screen locks are a form of endpoint device security control.
It manages user access to tasks and controls use of the devices. It offers a range of services for both personal and corporate use. View the security baseline settings that Microsoft Intune supports for devices that run Windows 10 and Windows 11.
The default values for settings in this baseline represent the recommended configuration for applicable devices. It also allows remote wiping of data in case device is lost or stolen. Endpoint Security for Mobile Devices.
Maximum minutes of inactivity until screen locks. Sign in to vote. Security inventory tracking and real time monitoring and reporting are key elements of an MDM.
Risk Threat X Vulnerability Which formula is typically used to describe the components of information security risks. Password access when not in use. Set the minimum security level and complexity of screen lock codes set maximum number of failed unlock attempts set the duration after which users must change their screen lock code.
The recovery point objective RPO is the maximum amount of data loss that is acceptable. For example the administrator can. Security baselines device configuration policies and endpoint security policies are all treated as equal sources of device configuration settings by Intune.
View Device Control Removable Storage Access Control data in Microsoft Defender for Endpoint. Learn vocabulary terms and more with flashcards games and other study tools. The lock screen of supervised iOS devices.
Defaults for one baseline might not match defaults from other security baselines or from other versions of this baseline. The asset tag for the device. When set to Not configured Intune doesnt change or update this setting.
To add or configure this policy go to Configure Device Policies. For more information see Device policies. Apple devices truncate long strings so be sure to test a string before deploying the policy to production.
Device Security Device security allows administrators to execute basic security policies across multiple mobile devices. At the same time these storage devices can be used to carry out sensitive data. Include requirements concerning mobile application management tools to ensure corporate apps and data are properly protected on the device.
Start studying Chapter 4. Devices that are managed by Configuration Manager dont display policy details. Mobile device tracking management and data protection available for laptops tablets and mobiles.

What Is Endpoint Security Endpoint Protection Dlp Currentware
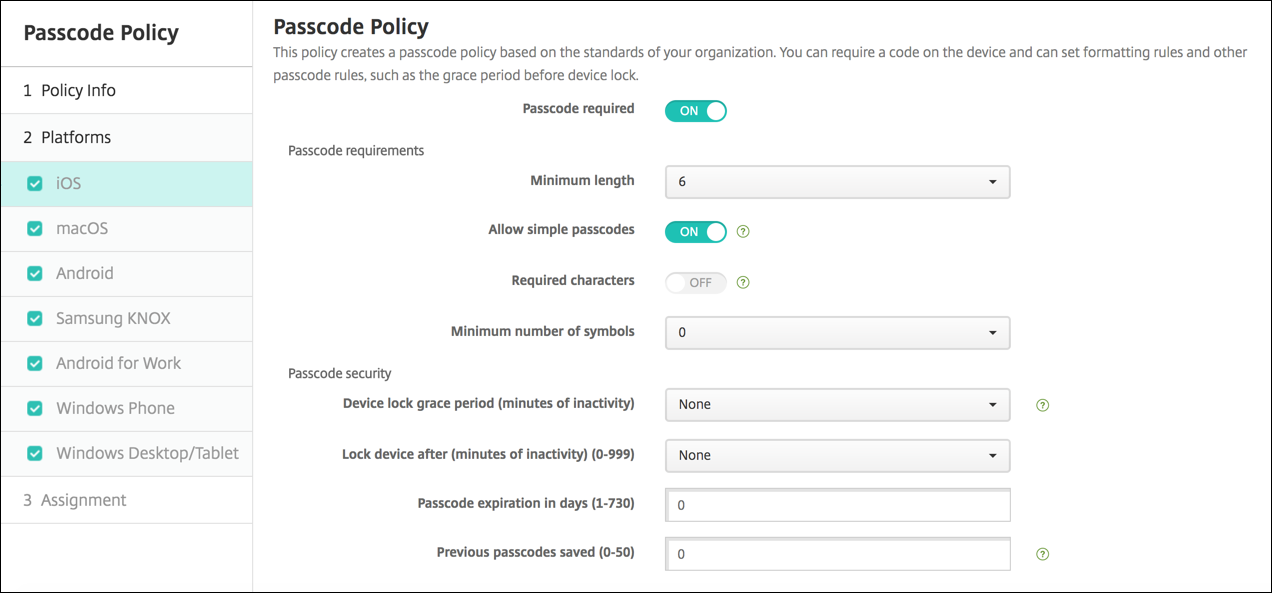
Passcode Device Policy Xenmobile Server Current Release

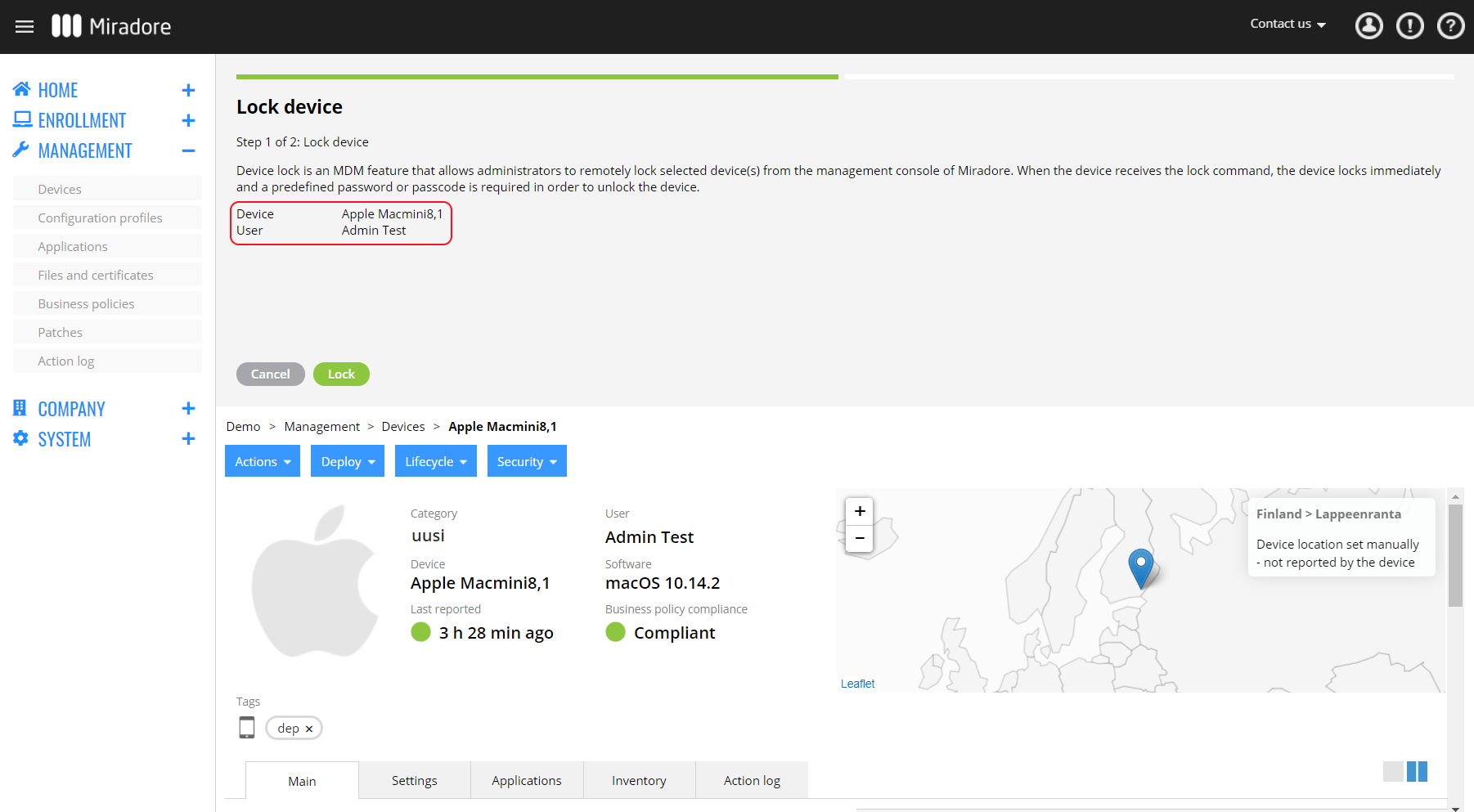
Remotely Locking A Device Miradore
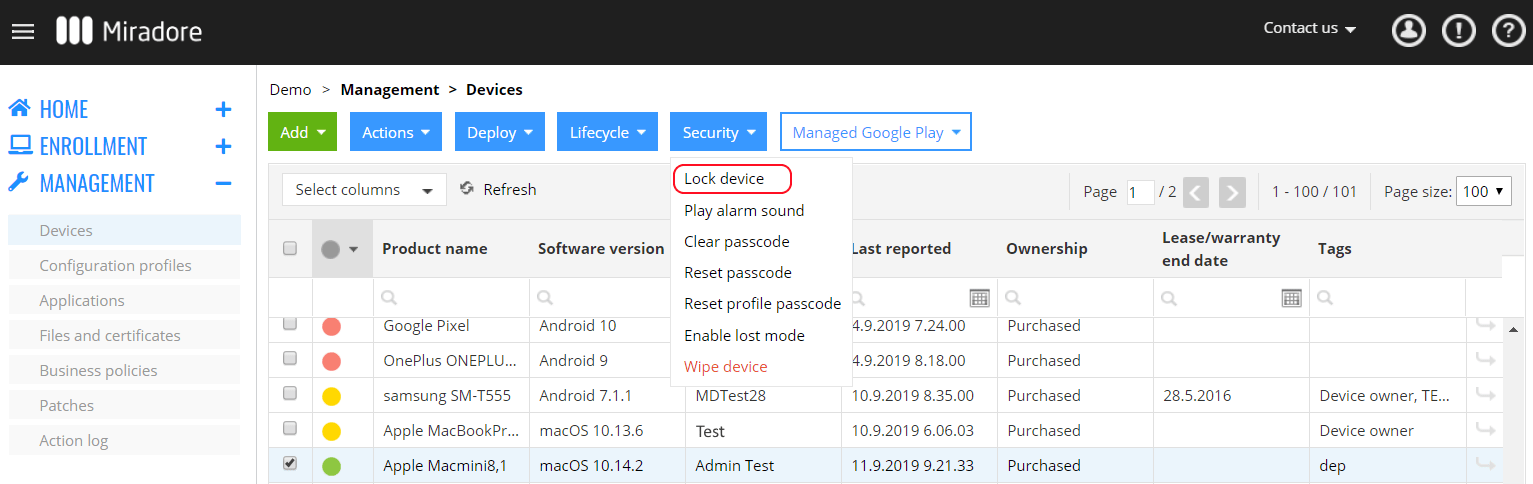
Remotely Locking A Device Miradore

Take Your Qnap Nas Offline Deadbolt Ransomware Locks Devices Via Alleged Zero Day Flaw

Download Avast Free Antivirus 2021 Which Is Better Avg Vs Avast Vs Avira Pop Up Ads Antivirus Software Antivirus
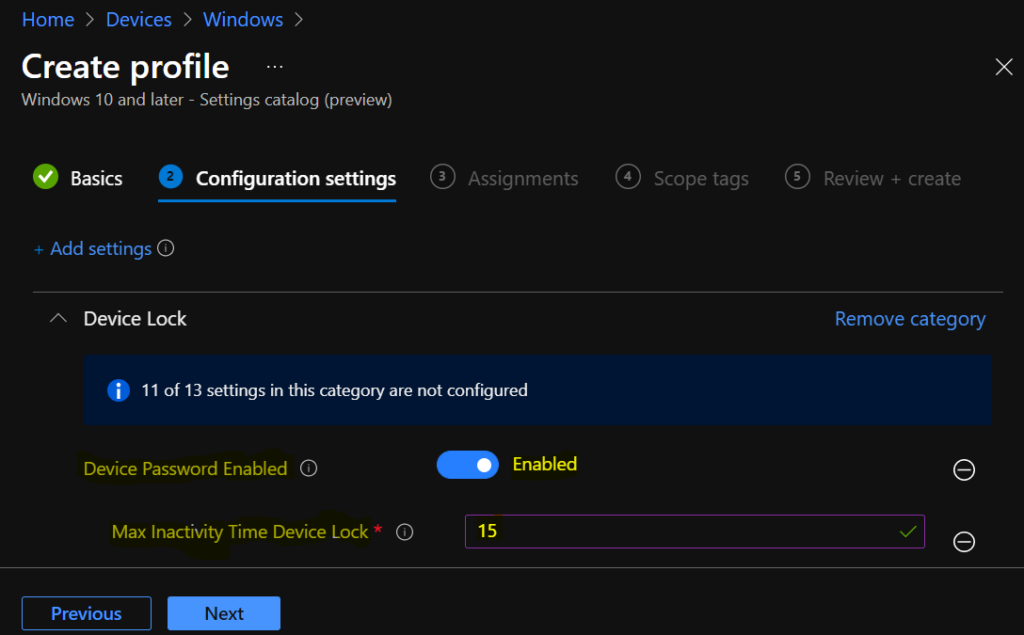
Easily Configure Automatic Lock Screen For Inactive Device Using Intune Htmd Blog
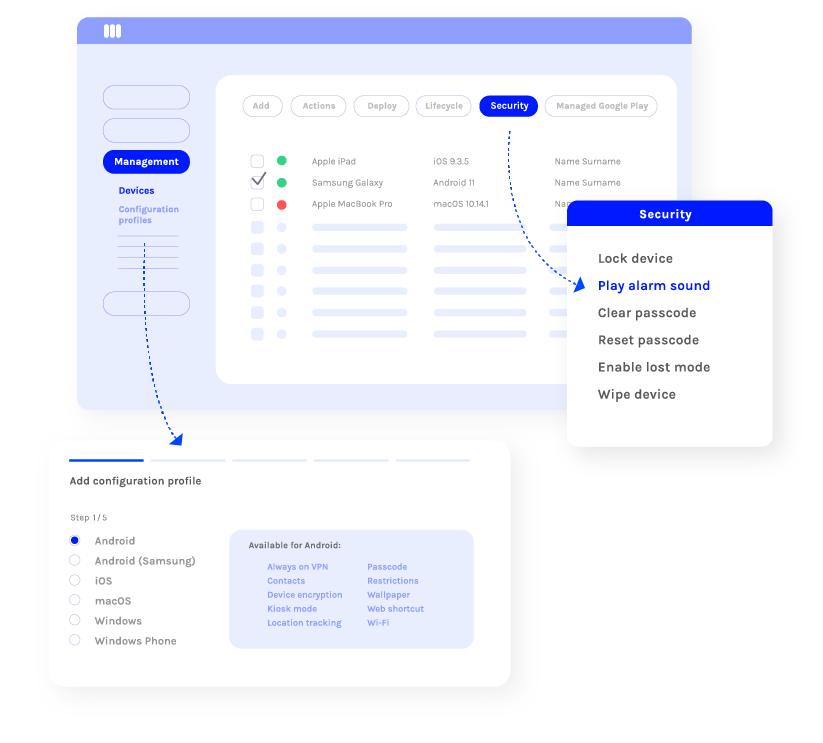
Device And Data Security Benefits Miradore
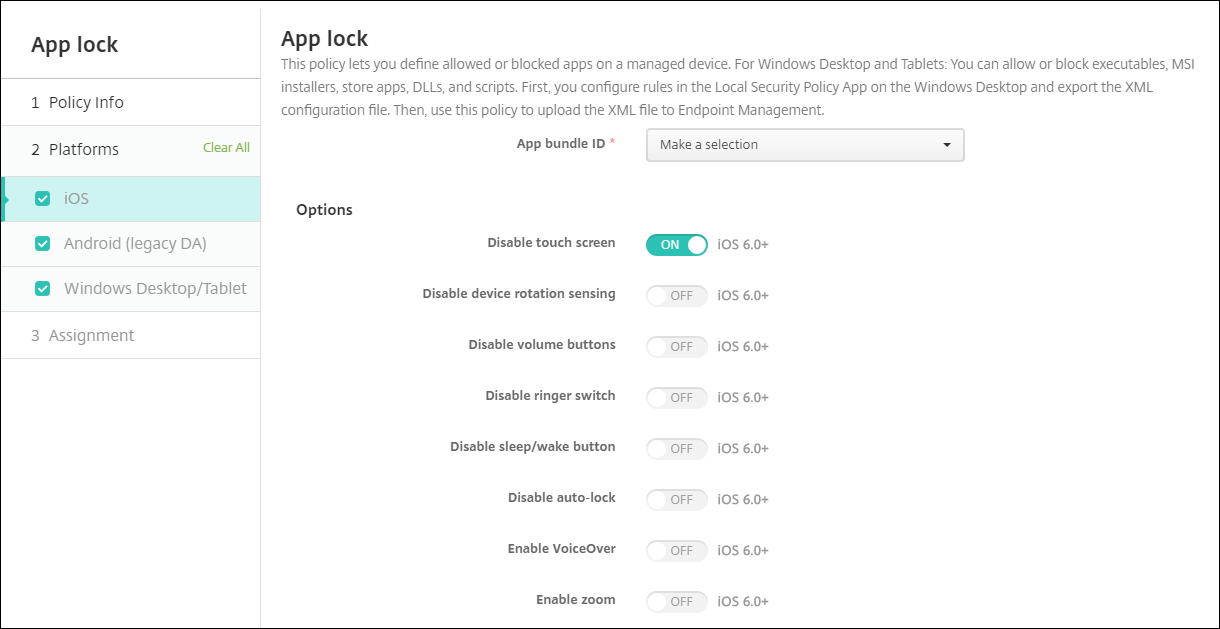
App Lock Device Policy Citrix Endpoint Management
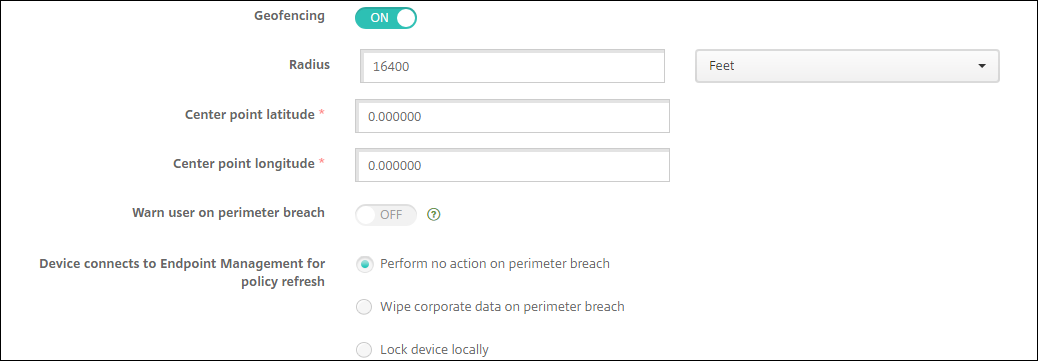
Location Device Policy Citrix Endpoint Management
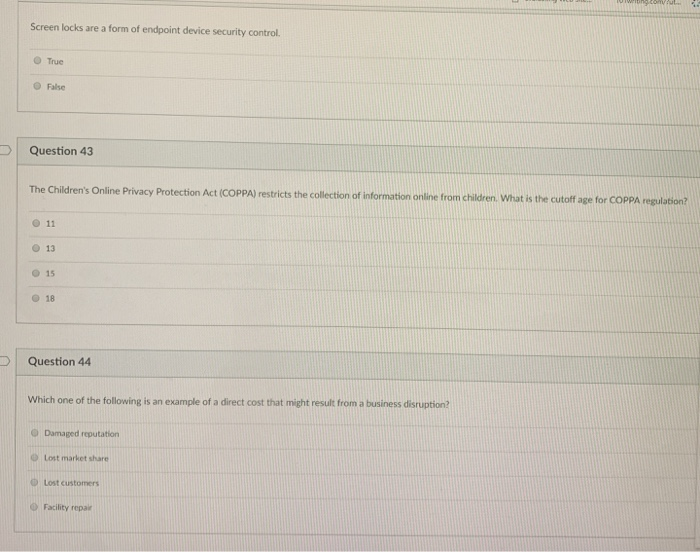
Solved Screen Locks Are A Form Of Endpoint Device Security Chegg Com

Tips For Secure Networks Computer Forensics Networking Analysis

Remotely Lock Your Device From The Intune Company Portal App Microsoft Docs

Zynn Short Form Video App Video App App Data Analysis Software

Panda Remotely Protects Manages And Supports All Of Your It Infrastructure Devices Including Tablets And Smartphones Prevention Infrastructure Technology

Configuring Windows Hello For Business Dynamic Lock All About Microsoft Endpoint Manager

Work Profile Set Up Stops At This Device Requires Secure Start Up Android Enterprise Community

Comments
Post a Comment